Observing Ransomware’s Evolution in Delivery Tactics
Written by Check Point’s Incident Response Team
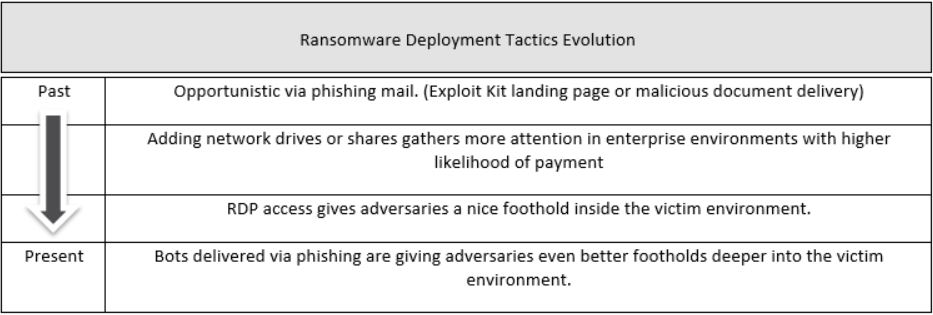
Four years ago, we used to joke about the likelihood of Cryptolocker being delivered to every single email address on the internet.
Back then, criminals would blast phishing emails to millions of email addresses, sending ransomware variants via infected links or Word Documents without any apparent rhyme or reason in their targeting. We saw everyone from students to grandparents, home users to IT professionals on corporate workstations fall prey to these attacks.
But when ransomware started encrypting network accessible resources, corporations started paying attention.
This stage of ransomware’s evolution saw that aforementioned scattershot delivery method combined with the feature of encrypting files on the local file-system and files on corporate server resources. The encryption of an infrastructure’s file server or Network Attached Storage system causes more damage to the enterprise than one individual workstation being encrypted. For this reason, our Incident Response Hotline started receiving more calls where IT Administrators of systems hit by ransomware started to ask very serious questions about the ramifications of paying the ransom.
This trend of ransomware encrypting network shares and the resulting heightened attention is likely what started the next phase of ransomware deployment techniques.
Precision Strikes: The Rise of Remote Desktop Protocol
As attackers started to interact more with their victims (due to the impact their ransomware had on the corporate environment), by 2016, we started seeing mass-infections of ransomware where several critical assets in the victim’s environment were infected simultaneously. Community intelligence prompted further investigation, which confirmed the community’s suspicion: criminals were using Remote Desktop Protocol, a Microsoft-designed proprietary protocol that gave users a graphical interface of a remote system, to gain footholds in the victim’s environment.
Once attackers establish their foothold, they typically deployed tools to help find and exploit misconfigured and unintentional user/group/administrator relationships. Misconfigured or unintentional Active Directory configurations are a cyber criminal’s best friend, because they allow the attackers access the domain administrator’s privileges. Once they compromise a domain administrator’s account, the attackers gain the ability to perform reconnaissance in the network in order to identify the most critical assets to infect.

After identifying critical servers and backup systems in the environment, the attackers can now use built-in Windows system administration tools to deploy any ransomware en masse.
Attackers were no longer trying to email every person on the internet – with Remote Desktop Protocol, they knew exactly where and what to target, infecting critical assets simultaneously thanks to their newfound access deep into the victims’ environments.

The Next Stage of Ransomware: Enter Botnets
The tactic of using RDP as the initial foothold for these en mass, scheduled, interactive or manual-deployments of ransomware was so common that it became our first line of questioning when taking on new ransomware incident cases.

However, with recent cases like the Ryuk ransomware [1], we are seeing another evolution of tactics. While investigating if victims have RDP exposed, we found either no RDP at all, or that RDP can only be accessed over VPN and is not exposed directly to the internet.
These cases required deeper investigations. In multiple recent cases, we are finding bot infections that correlate to the timeline of ransomware infections.
In the last month we have observed TrickBot, Emotet and AdvisorsBot infections that align perfectly with the time of ransomware deployment. These bot infections have been widespread inside the victim environment and also leveraged misconfigured Active Directory relationships to spread laterally.This trend toward using bot footholds is increasing.
In these cases, we have found phishing email containing malicious word documents to be the bot delivery vector. These malicious word documents contain executable content called macros. In TrickBot and AdvisorsBot infection investigations relating to ransomware we find that the victim has:
1. Opened the phishing mail
2. Opened the malicious document
3. Enabled macros to execute
At this point the executable content in the macros either installs a bot or it reaches out to botnet Command and Control networks for additional payload which ends up being the bot malware.
We see this as an evolution of ransomware deployment tactics. There is an observable trend in ransomware delivery from opportunistic phishing, to footholds and recon via compromised RDP, and today, advanced footholds deep inside the network via bot infections that spread laterally.
In conclusion, we believe this trend toward bot footholds used to distribute ransomware will grow. Different bots will be used over time but the fact that bots offer persistence and an easy method to deploy additional malware makes them an obvious choice for adversarial footholds.
The Check Point Incident Response Team is a vendor agnostic group of security analysts that help investigate attacks against both Check Point and non-Check Point customers. Let us know how we can help! [3]
Protection
- Check Point Sand Blast Agent Forensics, Anti Malware, and Anti Ransomware blades identify and stop bot and ransomware activity.
- Check Point Threat Extraction strips active content from documents and prevents bot infections that are delivered via malicious documents.
- Check Point Anti-Bot blade prevents post-infection command and control, removing a bots ability to communicate info gained during reconnaissance or download additional malware modules.
- Remote Desktop Protocol should not be exposed to the Internet. Only access RDP via a VPN and preferably with Two Factor Authentication.
- Evaluate Active Directory relationships to identify weak relationships between users, groups and administrators.
2. https://research.checkpoint.com/ryuk-ransomware-targeted-campaign-break/
3. https://www.checkpoint.com/support-services/threatcloud-incident-response/

The post When Ransomware Stopped Working Harder and Started Working Smarter appeared first on Check Point Software Blog.
from Check Point Software Blog https://ift.tt/2JdvBKO
via

No comments:
Post a Comment